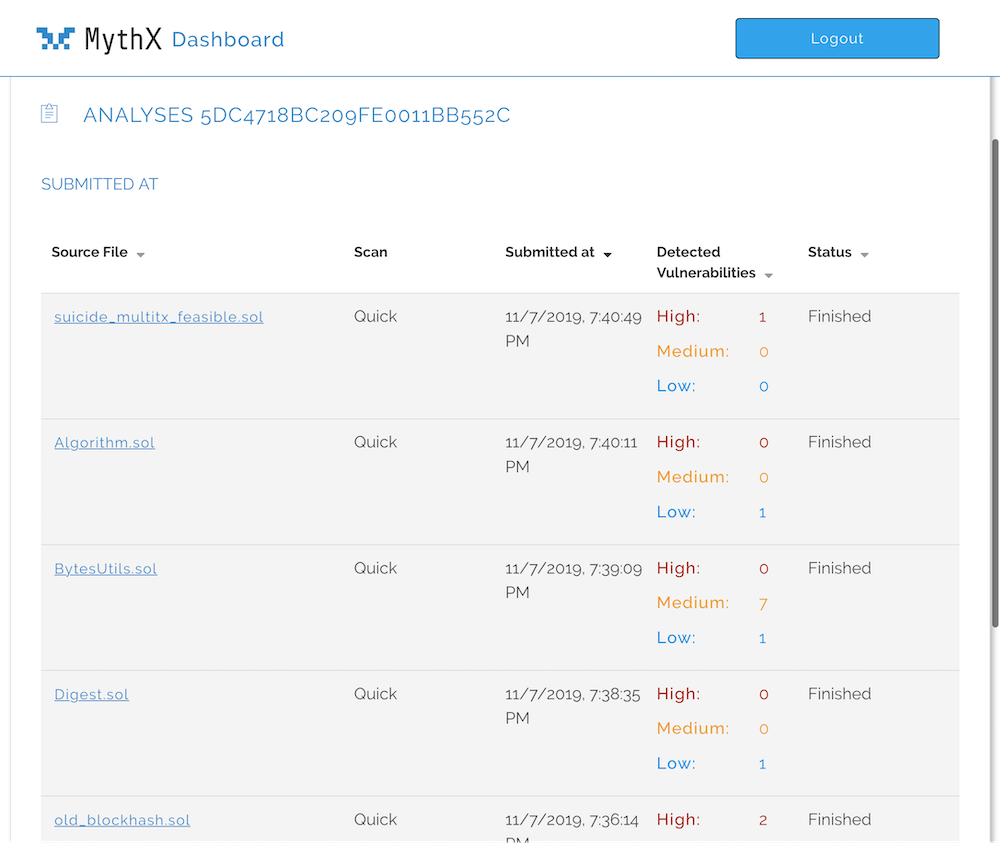
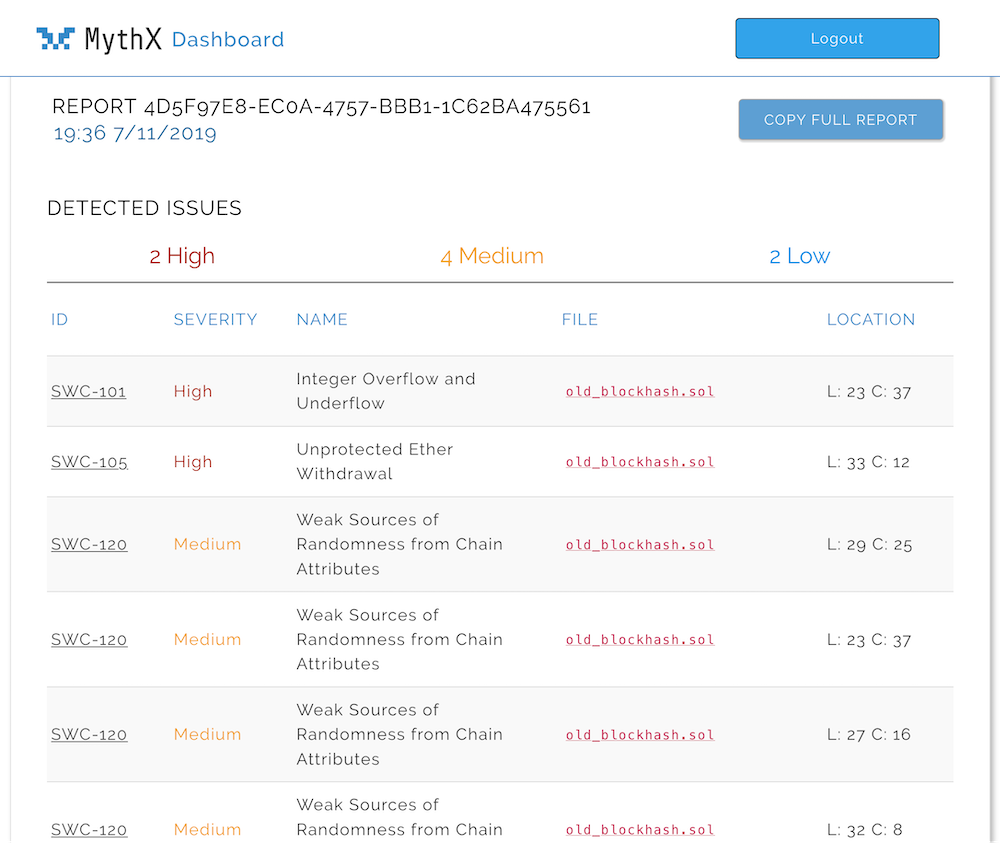
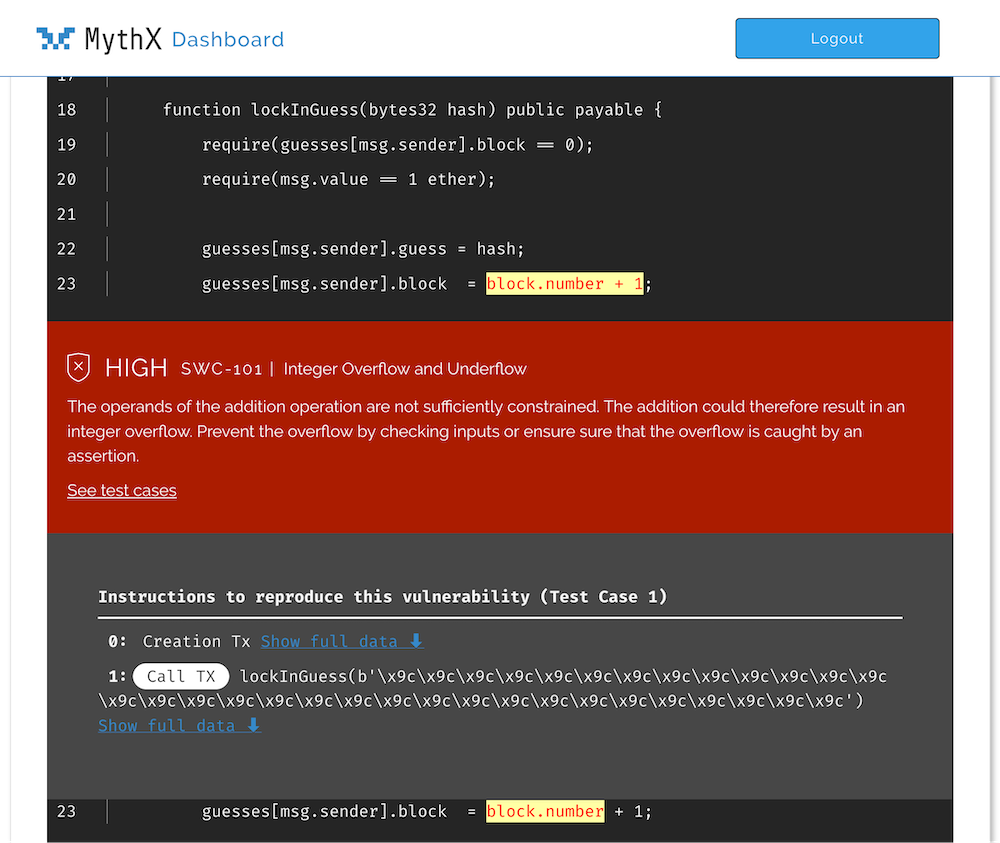
What happens to MythX?
MythX Components: Mythril remains open source, Harvey has evolved into Diligence Fuzzing, and Maru will be archived and may be open sourced in the future.
Alternative to MythX: Check out Diligence Fuzzing! Find bugs and secure your project with the most powerful fuzzer available.
New Dili Tools: Keep an eye on our Discord Channel for updates on our latest projects! We’re incredibly thankful for your support and hope you’ll continue the journey with us towards new beginnings.